Business Transformation, zBlog
Zero Trust Architecture: Redefining Enterprise Security in the Digital Age

In today’s digital landscape, where data breaches and cyber threats are increasingly prevalent, traditional perimeter-based security models have proven inadequate. The proliferation of cloud computing, remote work, and the expanding attack surface have necessitated a fundamental shift in how organizations approach cybersecurity. Enter Zero Trust Architecture (ZTA), is a strategic approach that challenges the notion of implicit trust and instead enforces strict access controls and continuous verification for every user, device, and application, regardless of their location or network.
As organizations embrace digital transformation and adopt distributed architectures, such as microservices and multi-cloud environments, the need for a comprehensive Zero Trust strategy becomes even more critical. By implementing Zero Trust principles, enterprises can effectively mitigate risks, enhance data protection, and maintain business continuity in the face of evolving cyber threats.
The Evolution of Zero Trust
The concept of Zero Trust was first introduced by John Kindervag in 2010. Kindervag recognized the limitations of traditional perimeter-based security models, which assumed that everything within the corporate network was inherently trustworthy, while everything outside was untrusted. This approach was no longer viable in an era where users, devices, and applications were increasingly distributed and the traditional network perimeter had become blurred.
Zero Trust Architecture emerged as a strategic initiative to address these challenges, advocating for a strict “never trust, always verify” approach. Instead of relying on outdated perimeter-based controls, Zero Trust focuses on continuously verifying and enforcing access policies based on multiple contextual factors, such as user identity, device posture, application risk, and data sensitivity.
The Principles of Zero Trust Architecture
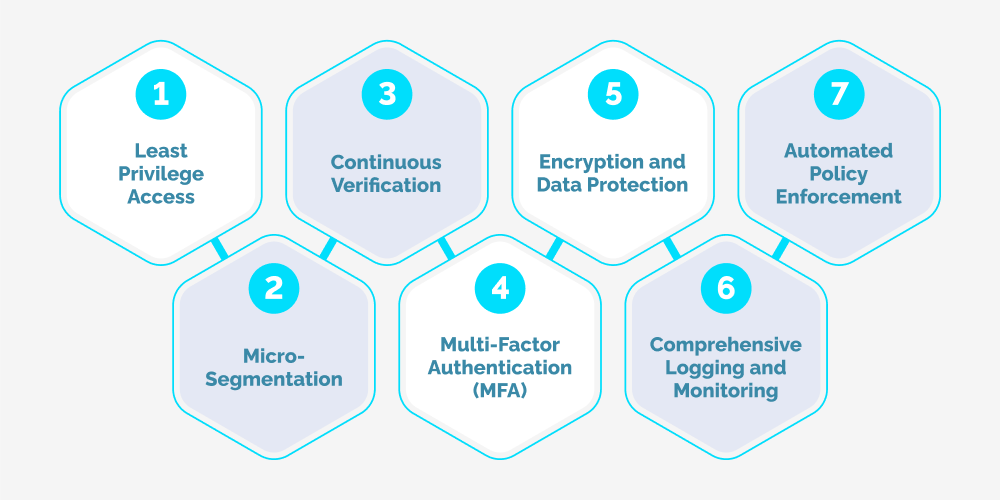
Zero Trust Architecture is founded on several key principles that guide its implementation and execution:
- Least Privilege Access: Access to resources and data is granted on a strict need-to-know basis, with users and applications receiving only the minimum necessary privileges to perform their intended functions.
- Micro-Segmentation: The network is segmented into smaller, granular zones or micro-perimeters, limiting lateral movement and containing potential breaches within a confined area.
- Continuous Verification: User and device identities, as well as access permissions, are continuously verified and validated throughout the entire session or transaction lifecycle.
- Multi-Factor Authentication (MFA): Robust authentication mechanisms, such as multi-factor authentication (MFA), are implemented to verify user identities and device posture before granting access.
- Encryption and Data Protection: Data is encrypted both in transit and at rest, with robust key management and access control policies in place to protect sensitive information.
- Comprehensive Logging and Monitoring: Detailed logging and monitoring mechanisms are implemented to detect and respond to potential threats or anomalous behavior in real time.
- Automated Policy Enforcement: Access policies and security controls are automatically enforced and adapted based on changing conditions, risk levels, and contextual factors.
The Benefits of Embracing Zero Trust Architecture
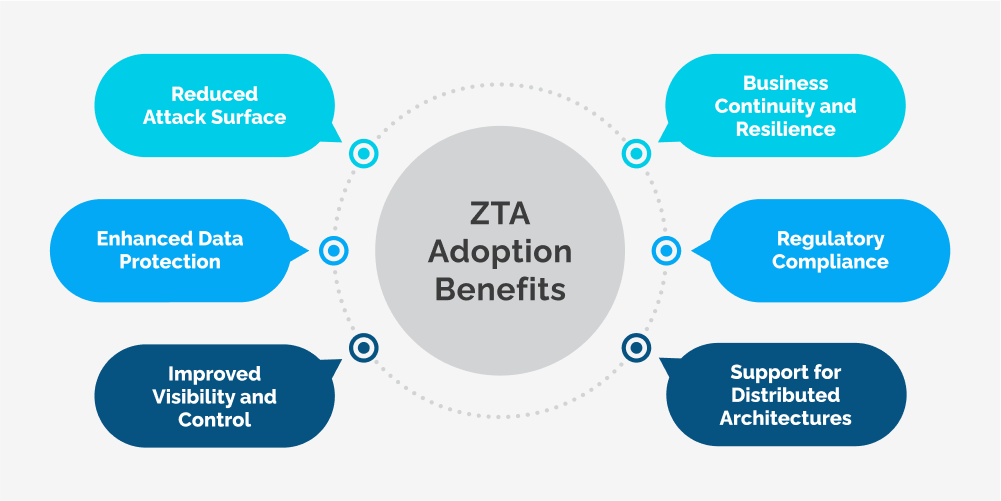
By adopting a Zero Trust Architecture, organizations can realize numerous benefits that enhance their overall security posture and enable secure digital transformation:
- Reduced Attack Surface: By eliminating implicit trust and enforcing strict access controls, Zero Trust Architecture significantly reduces the attack surface, making it more challenging for threat actors to gain unauthorized access or move laterally within the environment.
- Enhanced Data Protection: With robust encryption, granular access controls, and continuous monitoring, sensitive data is better protected against unauthorized access, theft, or manipulation, minimizing the risk of data breaches and compliance violations.
- Improved Visibility and Control: Zero Trust Architecture provides organizations with greater visibility into user and application activities, enabling proactive threat detection, incident response, and the implementation of adaptive security controls based on evolving risk conditions.
- Support for Distributed Architectures: The principles of Zero Trust seamlessly align with modern distributed architectures, such as microservices, multi-cloud environments, and remote workforce models, ensuring secure access and data protection across diverse and dynamic environments.
- Regulatory Compliance: By implementing robust access controls, encryption, and monitoring mechanisms, organizations can more effectively comply with various data privacy and security regulations, such as GDPR, HIPAA, and PCI-DSS.
- Business Continuity and Resilience: With improved security posture and reduced risk of breaches, organizations can maintain business continuity, minimize operational disruptions, and protect their reputation and customer trust.
Implementing Zero Trust Architecture
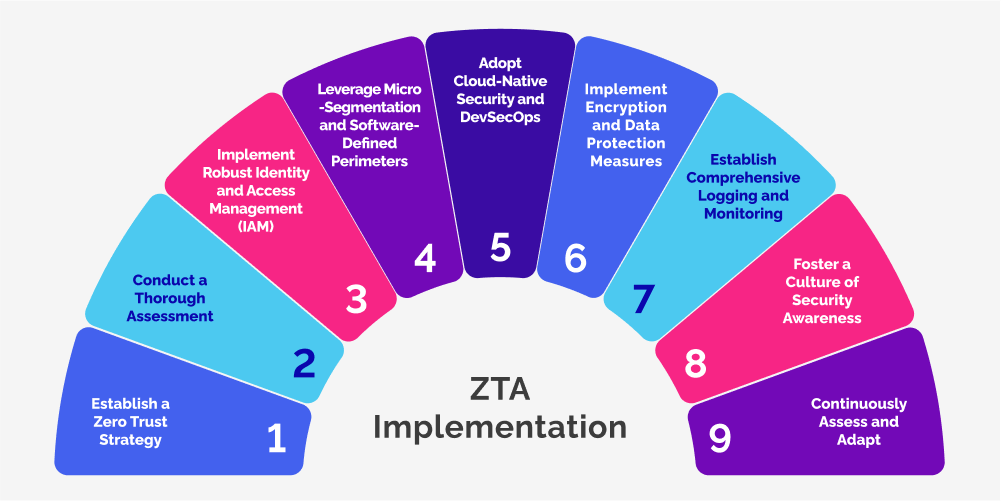
While the benefits of Zero Trust Architecture are compelling, its successful implementation requires a comprehensive and strategic approach that addresses people, processes, and technology. Here are some key considerations:
- Establish a Zero Trust Strategy: Develop a comprehensive Zero Trust strategy that aligns with your organization’s business objectives, risk appetite, and cybersecurity priorities. This strategy should define clear goals, principles, and a roadmap for implementation.
- Conduct a Thorough Assessment: Perform a detailed assessment of your current security posture, identify gaps and vulnerabilities, and evaluate your readiness for Zero Trust adoption. This assessment will inform your implementation plan and prioritization efforts.
- Implement Robust Identity and Access Management (IAM): Establish a strong foundation with robust identity and access management (IAM) solutions that support centralized user and device management, multi-factor authentication, and granular access controls.
- Leverage Micro-Segmentation and Software-Defined Perimeters: Implement micro-segmentation and software-defined perimeters to create secure zones or micro-perimeters within your environment, limiting lateral movement and containing potential breaches.
- Adopt Cloud-Native Security and DevSecOps: For organizations embracing cloud and modern architectures like microservices, adopt cloud-native security solutions and integrate security into your DevOps processes through DevSecOps practices.
- Implement Encryption and Data Protection Measures: Encrypt sensitive data both in transit and at rest, and implement robust key management and access control policies to protect critical information assets.
- Establish Comprehensive Logging and Monitoring: Implement centralized logging and monitoring solutions that provide visibility into user and application activities, enabling real-time threat detection and incident response.
- Foster a Culture of Security Awareness: Invest in security awareness training and education programs to ensure that employees understand and embrace Zero Trust principles, promoting a culture of security vigilance across the organization.
- Continuously Assess and Adapt: Zero Trust is an ongoing journey, not a one-time implementation. Continuously assess and adapt your Zero Trust strategy and controls based on evolving threats, emerging technologies, and changing business requirements.
Conclusion
At Trantor, a leading provider of digital transformation and cybersecurity solutions, we understand the critical importance of implementing a robust Zero Trust Architecture in today’s ever-evolving threat landscape. Our team of experienced cybersecurity experts, solution architects, and consultants possess deep expertise in Zero Trust principles, best practices, and industry-leading technologies.
We offer comprehensive Zero Trust services, guiding organizations through the entire journey – from strategy development and assessment to implementation, integration, and ongoing optimization. Our approach encompasses people, processes, and technology, ensuring a holistic and sustainable Zero Trust transformation.




