Cloud, zBlog
How to Build a Secure CI/CD pipeline using DevSecOps
trantorindia | Updated: August 16, 2022
Every software undergoes version upgrades through continuous integration of features, UI enhancements, database updates, and more. For each phase of the software development lifecycle, developers depend on multiple tools which facilitate a function or a set of related functions. Jira Software, for example, is a popular DevOps tool for planning and bug-tracking. Similarly, the various versions of a software product are kept on track via version control platforms like GitHub and Bitbucket.
This software development lifecycle is enabled by Continuous Integration/Continuous Deployment (CI/CD) pipelines that automate code building, testing, and deployment. As information technology increasingly embraces automation and cloud-native tools, the CI/CD pipeline has become a vital component of the DevOps workflows.
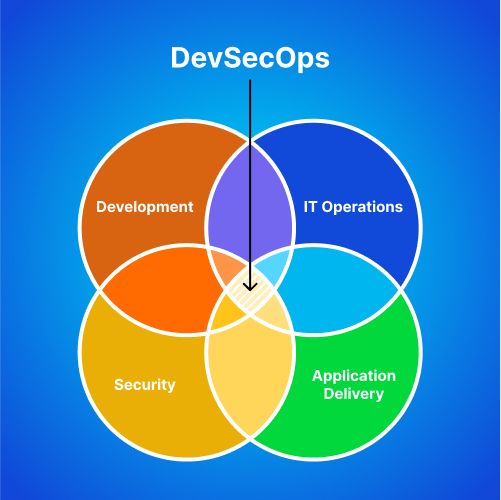
Although CI/CD pipelines increase the agility and efficiency of software development, integrating various tools can create security risks in the process. Development teams must recognize and plug these security loopholes to ensure a secure DevOps lifecycle. An efficient way to achieve this is to provide a security cover to DevOps using the best DevSecOps practices. Let us understand more about the security issues in a typical CI/CD pipeline and how DevSecOps can secure it from malicious attacks.
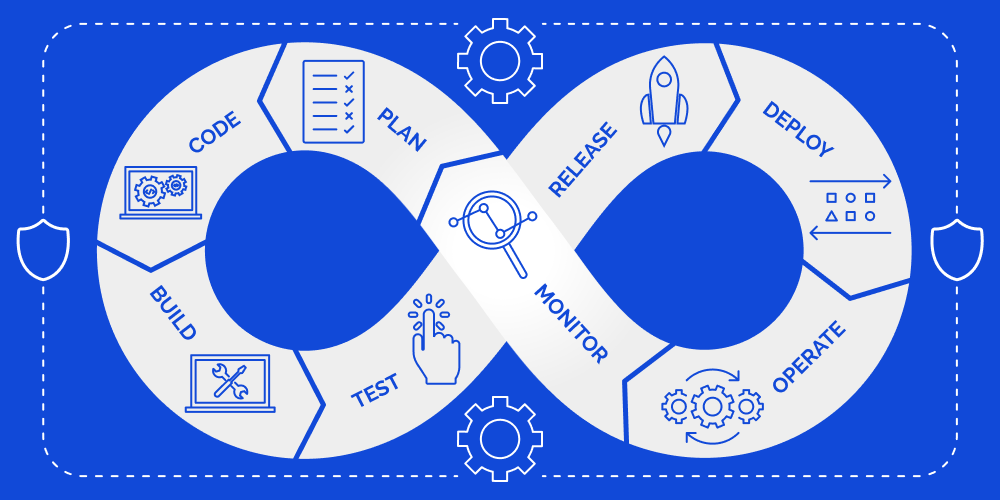
Legacy CI/CD pipeline in DevOps
A software product uses multiple microservices that depend on resources like databases. These form one layer of potential security threats. Furthermore, microservices can be within containers or use cloud computing infrastructure, thereby adding more layers of potential security threats.
In the legacy setting of the software development cycle, security was a separate unit from the CI/CD pipeline. Finding and resolving security bugs on production servers was a cost- and time-consuming affair. This led to left-shifting security activities and placing them before deployment for penetration testing, security scanning, bug hunting, etc.
Both these processes test for security loopholes, but since security testing could take days or weeks depending on software complexity, it also stacks up software versions waiting to get into the CI/CD pipeline.
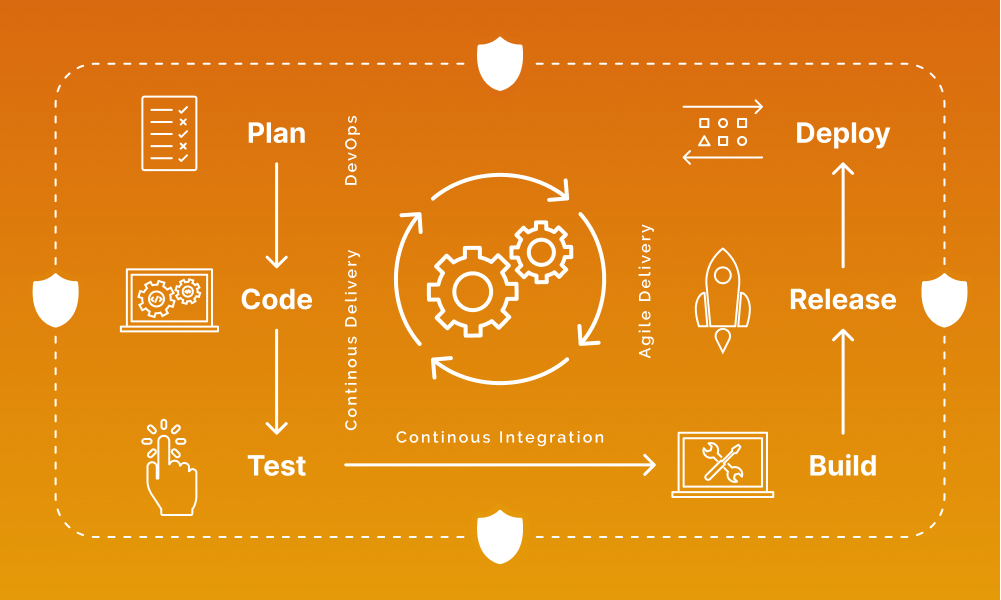
What is a Secure CI/CD pipeline?
A secure CI/CD pipeline integrates security throughout the software development process instead of selecting it before development or testing. The approach is to instill a security-driven mindset from ideation to deployment for all the stakeholders of a software product – product owners, product managers, developers, operations managers, and testers. It aims to create and implement security policies throughout the CI/CD pipeline and create secure product builds on platforms like Docker, Kubernetes, Ansible, Chef, or Puppet.
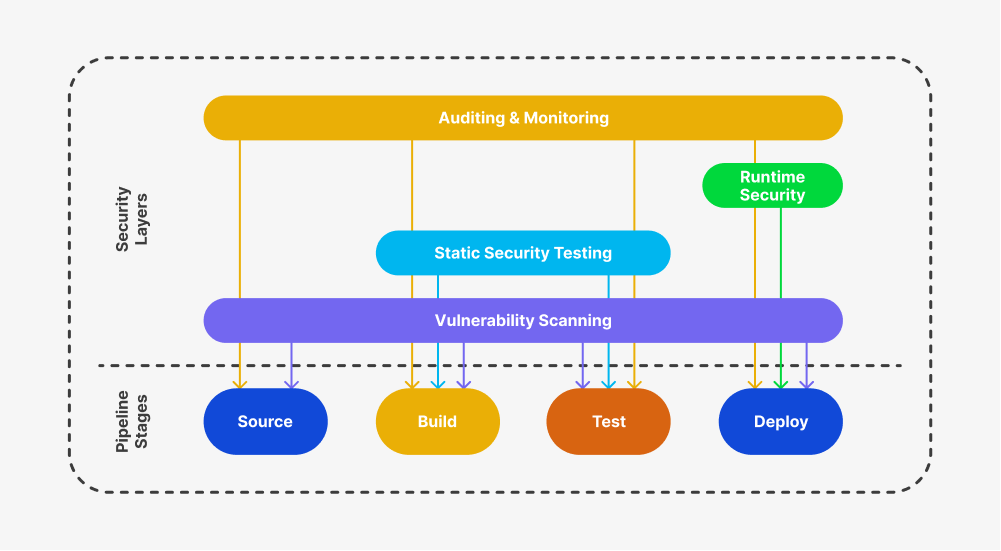
Steps Needed in DevSecOps
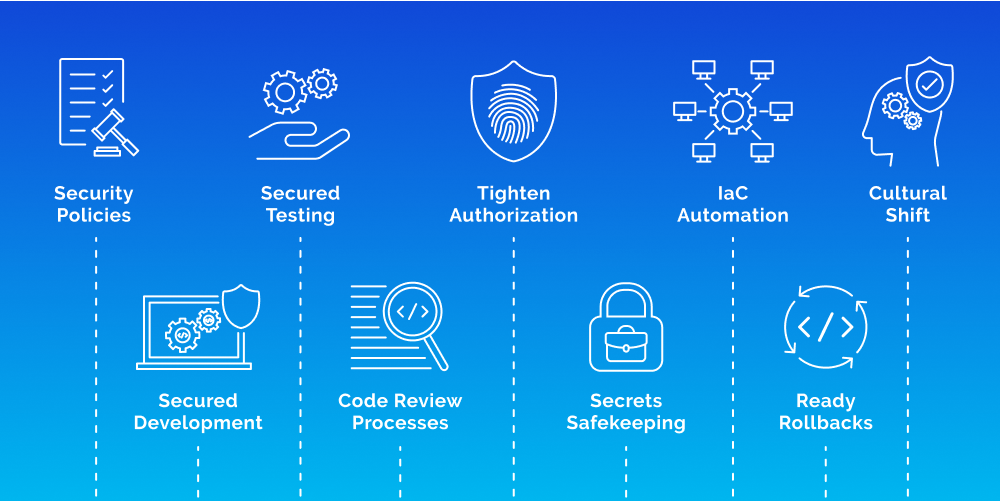
As mentioned earlier, every software product comes with layers, and each layer may contain lapses or security holes. This “Swiss cheese model” is exposed to threats from malicious attackers, thus requiring that each layer be well protected. Moreover, the production and testing environments use various databases, user credentials, proprietary code, passwords, etc., adding to the security risk.
Given the above risks, the following steps are necessary to help make your CI/CD pipeline more secure:
- Security policies: Security professionals can research and identify the scope for lapses in the pipeline. After that, issue guidelines to reduce those threats at each product development phase. It involves setting user and system-level policies for the development environment.
- Secured development: Developers may overlook security threats while building new features and pushing them into the production pipeline. In addition to the previous point, security professionals can provide developers with guidelines on developing more secure products and mitigating potential security threats at the code level.
- Secured testing: Automated testing with tools recommended by security professionals can reduce security threats for front-end, back-end, databases, and APIs.
- Code review processes: Peer review or code review from seasoned professionals can help mitigate security lapses in the development phase and train junior developers to approach coding with a security-driven mindset while meeting feature requirements.
- Tighten authorization: Clear definitions on who accesses what in the CI/CD pipeline. Regular audits to keep authorization or access to accounts or services in check and password rotation can also tighten security.
- Secrets safekeeping: Locations for authentication credentials, API tokens, encryption keys, etc., must have dedicated control, monitoring, and regular audits.
- IaC automation: Infrastructure as Code (IaC) automation reduces the additional responsibilities of managing servers, configurations, OS, etc., and provides a secure and consistent environment for development and testing. It reduces human errors and automates manual processes. Terraform, Ansible, Chef, and Puppet are a few leading names in Infrastructure as Code services, giving codified, managed security within the workflow.
- Ready rollbacks: Professionals across functions may put 100% of their efforts into making secured software products, yet security vulnerabilities may pop up. Thus, developer teams must keep backups of their stable builds for quick and easy rollbacks.
- Cultural shift: Companies must strive for a deliberate cultural shift by exercising security measures at each phase. Security is integral in software development with the growing number and variety of cyber-attacks. Employees must be trained on best practices for security by promoting a change in mindset.

Final Thoughts
Growing security risks in software development are already delaying rollouts of applications in more than 50% of organizations. Jenkins is a widely adopted DevOps platform for CI/CD implementation, along with a few others like Bitbucket and MABL, enabling seamless product releases. This necessitates adopting advanced strategies and tools to secure the CI/CD pipeline.
DevSecOps provides a solid framework for software products’ secure building, testing, deployment, and maintenance. With additional security practices at each phase of the CI/CD pipeline, all the stakeholders can push for secured versions and avoid costly security lapses in production. It is also pertinent that companies approach the software development life cycle with a security mindset right from ideation and teach it within their culture. With DevSecOps tools like Checkmarx, SonarSources, and Synopsys, security tends to be integral in the CI/CD pipeline.